Inspiration 💡
The advent of online education due to recent events has made it the new norm. Upsurge in the use of collaboration tools e.g., Google Meet eventually substituting business meetings, educational classrooms, and all sorts of social interactions has been noted.
But just like a double-faced coin, with the increase of shared technology usage for good, there has also been a surge of cybercrimes during this pandemic. Surveys state that, alone in the US, digital fraud attempts in 2020-21 have increased by 37.24%. Bad for us that we're now getting used to a new digital world to open a link sent by someone else without knowing if its contents are malicious or not.
In addition, it is estimated that cybercrime alone costs businesses worldwide $1.8 million per minute, and phishing amounts to the largest portion. However, applications of AI technology from various platforms can detect malicious links to save the business approximately $9 for each detection.
We decided to make let you know whether R U Safe by keeping users safe without needing to spend energy checking if a link is safe or not.
What it does 🤔
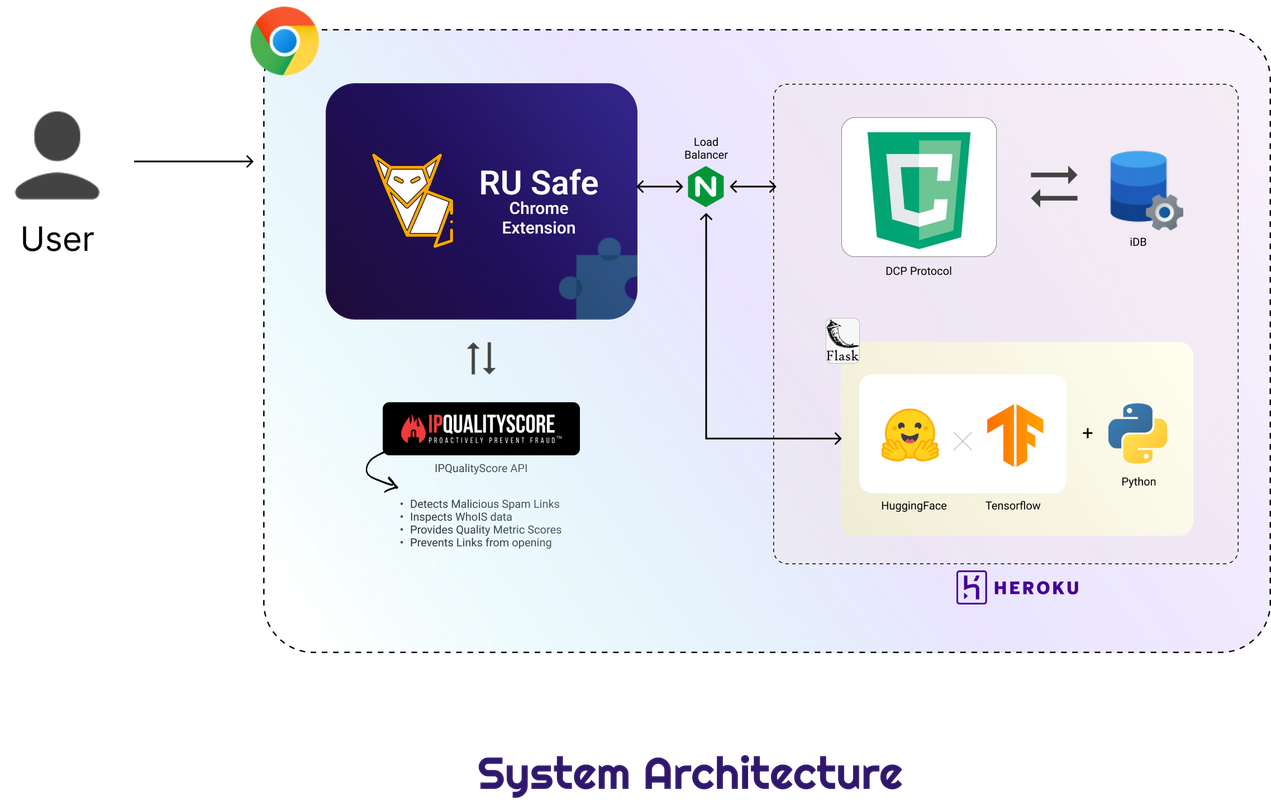
The R U Safe Chrome extension ensures that users can surf the web without needing to worry about links to malicious websites. The extension immediately terminates any tab that leads to a malicious website. By analyzing links using a Machine Learning algorithm trained with Google’s Tensorflow software library, R U Safe is able to reliably detect malicious websites.
How we built it ⚙️
For the Chrome extension, it uses front-end HTML, CSS, and JS, which also connects to the list of untrusted sites (hosted on a Heroku app). This list of untrusted sites is regularly updated using the ML model using Tensorflow in Python. This implies the extension will automatically evaluate all links before navigating to them.
The DCP API is used to optimize the response speed of the chrome extension. It lets us perform the malicious link checks in the background. This makes the extension respond much faster upon clicking the link as all of the computation has been done beforehand, making the response time unnoticeable. DCP also balances the workload on multiple systems, increasing system responsiveness and stability.
Research 📚
These sites provided vital information in helping us realize how large of an issue cybersecurity is, and its Updated 2022 Phishing Statistics Phishing Attacks Targeting Young Adults
- Learning Opinion Summarizers by Selecting Informative Reviews, ArXiv : https://bit.ly/3npVjC7
- Learning to Summarize Long Texts with Memory Compression and Transfer, ArXiv : https://bit.ly/3karaEV
♣ Datasets :- Recompiled from several sources.
♣ Articles :-
- Fraudsters tricking people with Google Meet, IndianExpress : https://bit.ly/3alDHj3
- Google Meet’s Open redirects can lead the user to a spoof website where they may become victims of phishing, Digitalinformationworld : https://bit.ly/2X2tsx0
- More and more phishing scams are using Google Meet, Techradar : https://bit.ly/3my9enu
- COVID impact on meeting apps, CNBC : https://bit.ly/3iNdnms
CREDITS
- Design Resources : Freepik
- Icons : Icons8
- Font : Fredoka One / Manrope / Montserrat / Roboto
Challenges we ran into 😤
We were all online and separated by a 10 hour time zone difference, as such, it was difficult for us to communicate during the Hackathon. We also spent a great deal of time brainstorming and discussing project ideas. In addition to this, 2 of our members were completely new to hackathons and required some time to get accustomed to the fast-paced environment.
In addition, the integration of different libraries and APIs proved to be challenging but also exciting. Utilizing the DCP in the chrome extensions which did not support the conventional importing of JS files.
Accomplishments that we're proud of ✨
A working browser extension that silently protects the user on the web. It has been a wonderful journey working with our team. Since the extension functions properly, it is a great milestone for us to have met. We could not have done it without the webinars and feedback from all the representatives.
In addition to this, our beginners adapted to the environment very quickly and worked well with the group to produce a fully functioning application within the timeframe. We were able to assign the work for each person according to their strengths and weaknesses, which allowed us to create our project.
Implementing DCP to our project to both make our extension run seamlessly in browsers and increase its responsiveness and stability.
What we learned 🙌
- The function and use case of DCP, and how parallel processing benefits specific tasks
- How we can use Machine Learning to be able to identify malicious links to prevent phishing and other malicious attacks
- Using Chrome extensions to make an accessible service to all Chrome browsers

What's next for R U Safe? 🚀
- In general, we will provide more safety evaluations for other types of objects. For example, images would be able to be scanned if they have injected code that can be dangerous.
- Users may be able to whitelist trusted pages.
- Dangerous websites may instead show a prompt detailing why it has been blocked, and can let users choose to continue visiting the malicious site.
Note — API credentials have been revoked. If you want to run the same on your local, use your own credentials.
Built With
- css3
- dcp
- github
- html5
- javascript
- sublime-text
- tensorflow








Log in or sign up for Devpost to join the conversation.